Securing Cross-Chain Applications
Using Zero-Knowledge Proofs
 Instituto Superior Técnico
Instituto Superior Técnico  INESC-ID
INESC-ID  Blockdaemon
Blockdaemon  Metacraft Labs
Metacraft Labs Source (PDF) tbd
Code DendrETH Repo, Trusted Data Transfers with Harmonia x DendrETH
Presentation DPSS Presentation, Dec 2023
In this instantiation of Harmonia, DendrETH implements an improved version of Ethereum's light client sync protocol that fixes previously known critical security flaws. This light client protocol is implemented as a smart contract, allowing blockchains to read a source blockchain's state in a trust-minimized way. This enables the creation of several cross-chain use cases, such as secure cross-blockchain bridges (asset transfers) or smart contract migrations (data transfers) that do not require a trusted operator.
Our implementations are compatible with the Ethereum Virtual Machine (EVM) based chains and some non-EVM chains. We provide an open-source implementation and reproducible environment for researchers and practitioners to replicate our results.
Advantages Compared to Other Interoperability Approaches
Cross-chain systems facilitate reliable and streamlined interactions between distinct blockchains, as our previous research shows. The consensus in the blockchain realm is leaning towards a future dominated by multiple chains. Numerous projects focusing on cross-chain bridges are currently operational. But, a large number of them are either not optimized for performance or lack robust security measures. As of October 2023, malicious entities have managed to exploit these bridges, leading to a loss of over $2 billion. We aim to improve the robustness of interoperability, paving the way for a new paradigm of developing cross-chain applications. We gain:- Inherent Trustworthiness and Robust Security: Using zero-knowledge proofs - thus no external trust assumptions are introduced.
- Open Participation and Distributed Nature: Any node has the autonomy to connect with the network, relay block headers, produce proofs, and secure rewards.
- Adaptable and Extensible Design: Harmonia-powered applications can introduce their unique verification processes and functionalities, enhancing their breadth of application (e.g., transaction validation via supplementary Merkle proof). By distinguishing the interoperability mechanism from the cross-chain logic, Harmonia simplifies the integration of decentralized applications with several blockchains.
Technical Overview
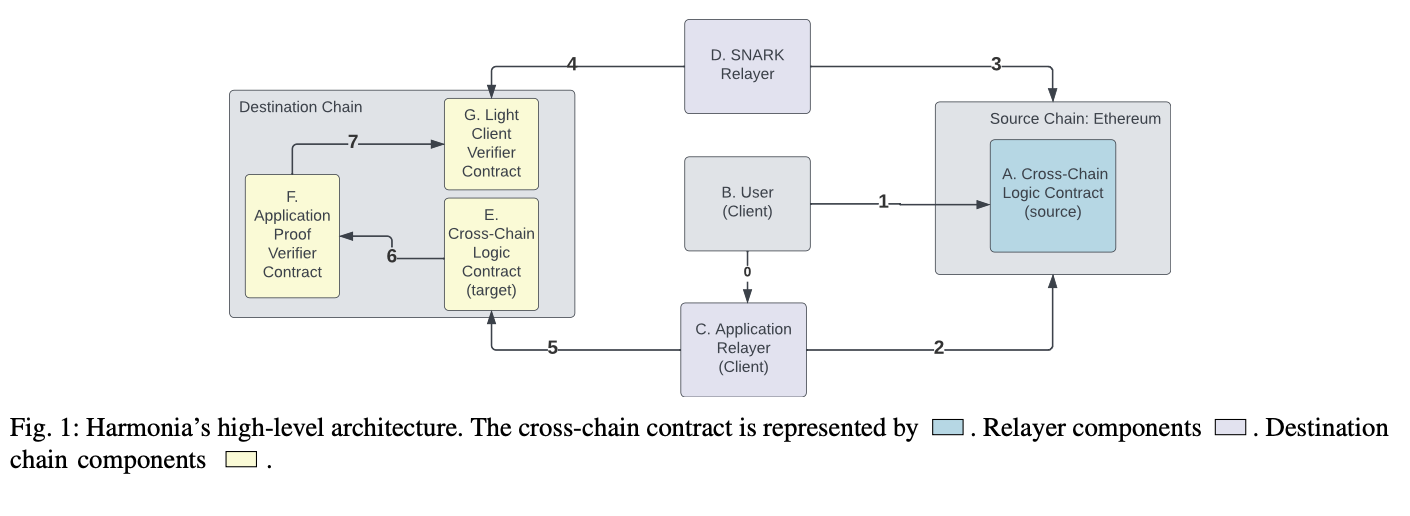
The starting point is a pair of cross-chain smart contracts (A and E). The contract E will have read and/or write dependencies on A, depending on the defined cross-chain logic. Then, in steps 0 and 1, user B interacts with the source chain smart contract directly or via the Application Relayer (respectively), issuing transactions that change the local state of A - therefore we deem them blockchain clients.
The Application Relayer (C) will see changes to the contract in step 2, and create a Merkle proof that attests to the state changes that step 1 triggered. The Merkle proof and use-case-specific data are sent to E according to the cross-chain logic - see our paper on this. In parallel, the SNARK Relayer gathers the light client state and data (step 3) to create a zero-knowledge proof proving a light client update. The SNARK, along with the necessary input data are sent to the light client verifier contract (G), which is a SNARK verifier contract (step 4).
If the verification succeeds, the necessary data to validate Merkle proofs will be available on the smart contract, to be consumed by applications. The Application Relayer can transact with E following determined cross-chain logic (step 5). The cross-chain logic contract on the target chain will only execute the logic if the Merkle proof verification on the Application Proof Verifier Contract (contract F) succeeds (6). Contract F calls the SNARK verifier to obtain validated state roots to run the Merkle proofs against.
DendrETH Specification
We specify improvements to the Altair Light Client Protocol, which we incorporate in DendrETH. DendrETH is a smart contract implementation of Ethereum’s light client protocol. DendrETH then allows proving Ethereum facts on target blockchains (we leave the other way around to future work).
The core of DendrETH proposal is to make the sync committee accountable by creating and sharing evidence that can lead to slashing. The idea is if the sync committee signs and submits an alternative finalized history, the entire sync committee gets slashed. Only malicious behaviour should be slashable - “but a validator that is simply tricked into syncing to an incorrect checkpoint should not be slashable even though it is participating on a non-canonical chain.
DendrETH then relies on a set of relayers, which are defined as follows: